A bug in Grammarly’s Google Chrome web browser extension was exposing all of your documents to virtually anyone or any website that wants to view them. If you’ve used Grammarly’s Chrome extension, all of the documents (including websites, documents, MS Word documents, including Microsoft Office documents) have been exposed to the public.
If any of the documents that you’ve used Grammarly on to check spelling or plagiarism are of a sensitive nature, then you probably should be concerned about this security breech.
Update: this has been fixed and user login details are no longer exposed. However, if you have any documents that are of a sensitive nature in your Grammarly account then you may want to remove them. Also, in any case like this, I urge you to go change your login details (change your password) at Grammarly.
Grammarly’s Auth Tokens Exposed
The problem was that Grammarly’s auth tokens have been exposed to all websites through their Google Chrome web browser extension. Essentially, a simple script (JavaScript code) installed on a website could get a grauth token (a Grammarly authorization token), and that grauth token matched the grauth cookie used on grammarly.com That meant that anyone with the grauth token could log into your Grammarly account, accessing all of your documents.
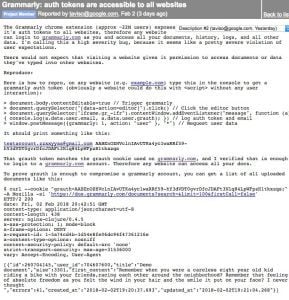
A bug report was added to bugs.chromium.org, detailing the issue:
I recommend that, for now, you uninstall the Chrome web browser extension on Grammarly unless you absolutely need it, and stop using Grammarly on highly sensitive documents. Then, log into your Grammarly account and review the documents there to be certain that there aren’t any documents there that contain sensitive content. And, as mentioned above, change your password at Grammarly.
Grammarly currently has about 22 million users.